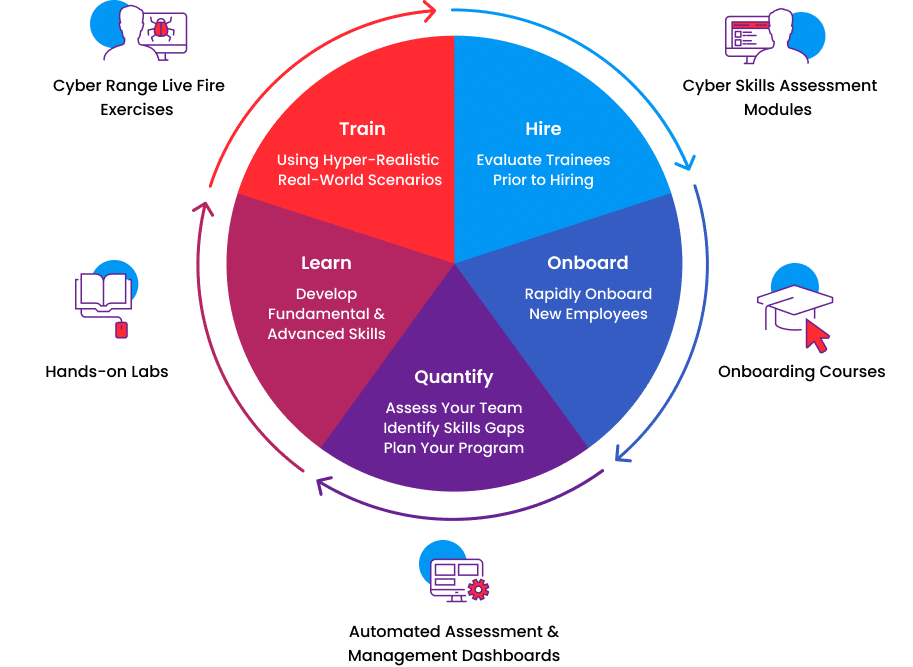
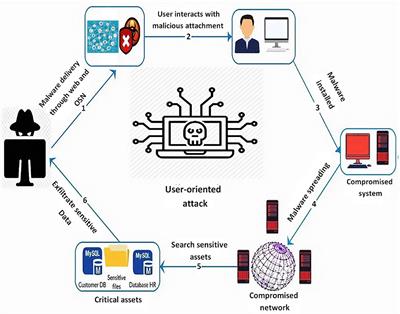
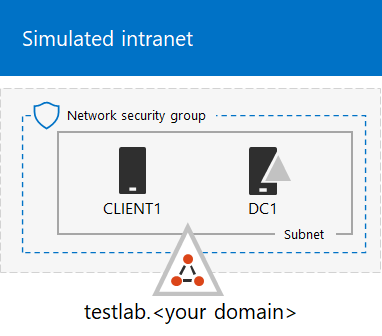
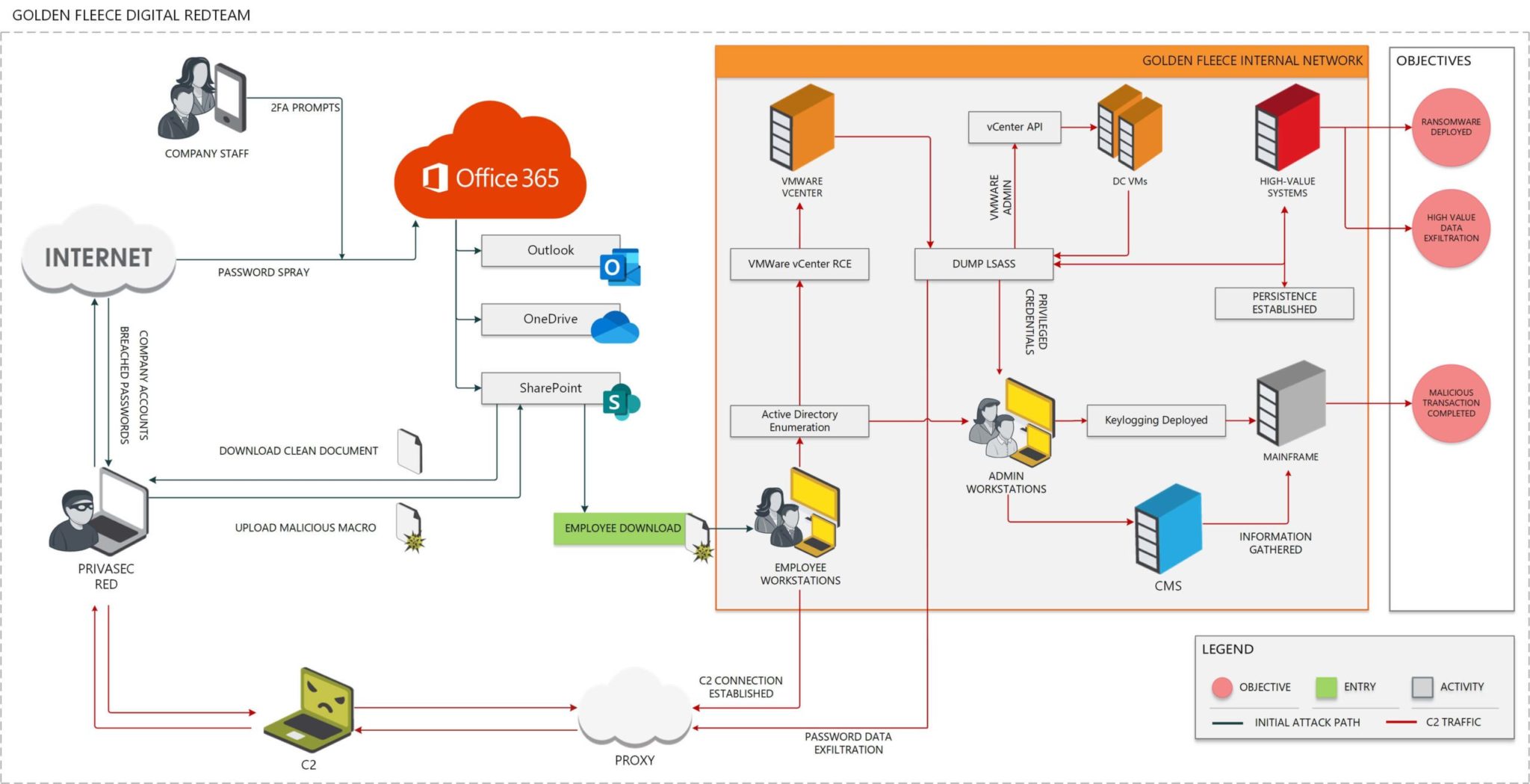
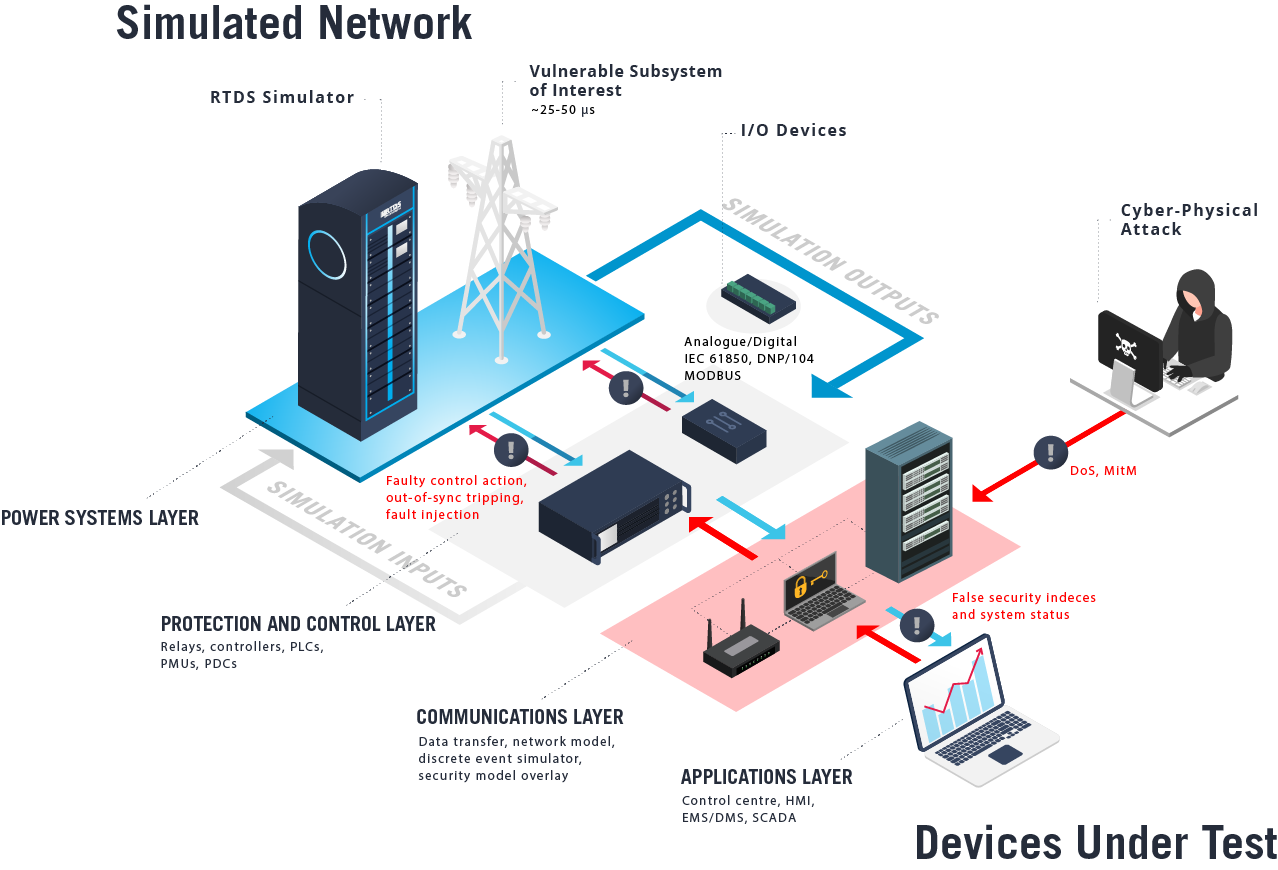
Cyber threat assessment via attack scenario simulation using an integrated adversary and network modeling approach | The Society for Modeling & Simulation International
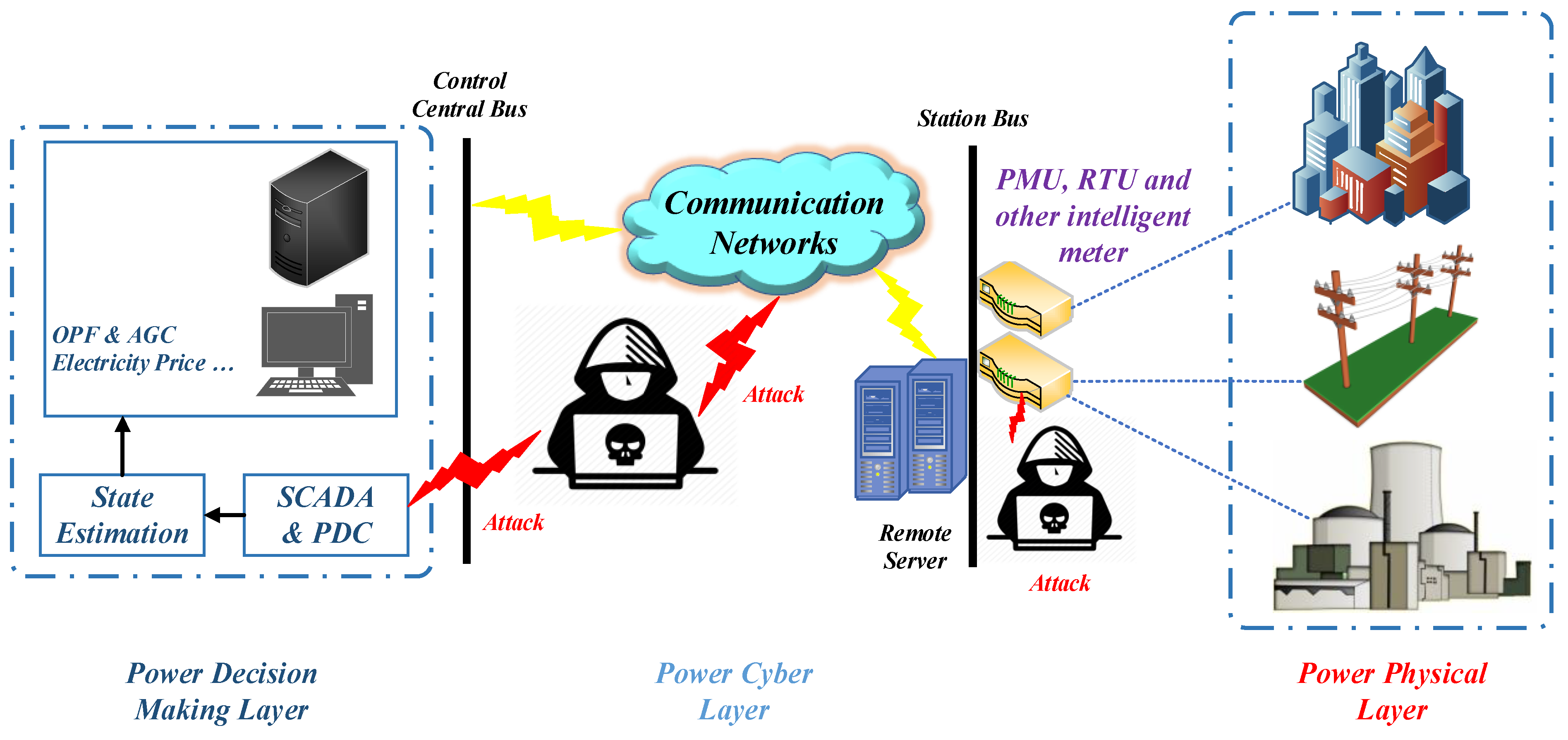
Mathematics | Free Full-Text | Deep Machine Learning Model-Based Cyber- Attacks Detection in Smart Power Systems
![PDF] Probabilistic Modeling and Simulation of Vehicular Cyber Attacks: An Application of the Meta Attack Language | Semantic Scholar PDF] Probabilistic Modeling and Simulation of Vehicular Cyber Attacks: An Application of the Meta Attack Language | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7843ee4ddfa611120b56a7acaaa54f7f764a685b/7-Figure2-1.png)
PDF] Probabilistic Modeling and Simulation of Vehicular Cyber Attacks: An Application of the Meta Attack Language | Semantic Scholar
Network diagram of deauthentication attack simulation with external... | Download Scientific Diagram
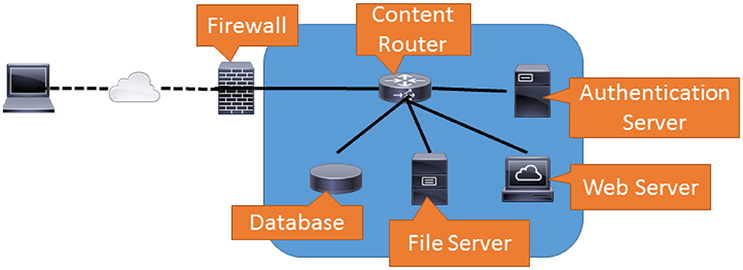





![PDF] Cyber attack modeling and simulation for network security analysis | Semantic Scholar PDF] Cyber attack modeling and simulation for network security analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1729573578805492cdcc7edebaae3ee7d79b93a0/3-Figure1-1.png)